I gave a talk at SnowFroc 2024 providing:
- an overview of the new SEC cybersecurity disclosure rules
- analysis of 8-K and 10-K disclosures since the new rules took effect
- some early on “best practices” for cybersecurity risk management, strategy, governance and how to develop compliant and high quality SEC filings.
I’ve posted a re-recorded version of the talk on my YouTube channel (my attempt to record on my iPhone at the conference was a fail) as well as the slides and transcript below. I’ve also uploaded a PDF of the full slides.
Table of contents
Introduction
Hey everybody, my name is Andrew Hoog and I’m the co-founder at NowSecure where we help companies manage mobile app risk through automated assessments of the apps they build and the apps they use. And I’m actually re-recording this talk because we had audio-visual issues at SnowFROC 2024 and I just wanted to post this on YouTube as well.

So I’d like to talk to you about cybersecurity risk and this is a bit of an odd topic for me because typically I’m talking about mobile security, DevOps, security test automation, GitHub actions, but I recently joined the board of trustees at my alma mater, St. Louis University, and I really wanted to figure out how to be a better board member. And so that kind of started me on a journey where I first went out and looked at things like enterprise risk management. Didn’t really know a lot about it, wasn’t an area that I was super interested in. And enterprise risk management got me looking into the SEC a bit more and that’s when I learned about the new rules coming out in December of 2023 where companies would have to post cybersecurity incidents as well as information about their governance, their risk management, basically how they’re approaching cybersecurity. And so I became really interested in that because I’d like to tinker and write code on the side. I went ahead and built some parsers so I could basically pull that information down.
And professionally, I’ve been taking a harder look at enterprise risk to try to understand why companies seem to generally overlook mobile app risk. Clearly a company’s mobile app can drive significant revenue and stickiness. Starbucks is a great example - they shared that in Q1 FY24, mobile orders represented 31% of all transactions (net revenue was $7.1 billion). But what we see in the market is mobile app risk is largely an afterthought, perhaps due to the incorrect assumption that the App & Play Stores perform sufficient security testing of mobile apps. Also, I suspect security teams believe that existing testing technologies used for web apps provides good coverage of mobile app issues. While web testing vendors do market this, I can tell you first hand those techniques miss the majority of mobile app risk. So, that’s the other part of the journey, seeking to understand high to tie the highest levels of enterprise risk directly to key technologies driving growth.
This talk will walk you through some background on the SEC disclosures, findings that I’ve had from the different 8-K and 10-K analysis that I’ve done, and then some best practices that, hey, I’m not an expert, I’ve never actually filed one of these, but just from reading a bunch of them, some best practices that I’d love to share.

So why should you orient to risk? Well, I’m largely a cybersecurity practitioner. I started this company 15 years ago, I co-founded it with my spouse, and we actually started out in forensics. So I have two books on the topics of forensics and security. I have three patents in the area. And as you can tell, I’m really on the technical side. And so I haven’t thought as much about risk, but increasingly I’m realizing this is a really important topic for security professionals to understand.
So first of all, you’re going to be much more effective at communicating security issues if you talk to the rest of the business about risk versus, let’s say, a CVSS score.
If you can put things in terms of the overall risk that they’ve already defined, then you don’t have to spend as much time trying to convince folks that they should work on something or maybe have them dismiss you because they don’t really understand what you’re saying or your background or they’re intimidated by it.
The second thing is this can really help accelerate your career depending on what your objectives are.
So if you want to move up in an organization, if you’d like to ultimately be a CISO or move into the C-suite or maybe eventually have a go on board of directors, then you really have to understand how to think about and talk about risk because risk is really the language of the C-suite and of the board.
They’re constantly managing risks against financial reward.
And then the last thing that I would share is that we’re all impacted by risk.
We think back to things like Enron or the dot-com bubble or all the way back to the stock market crash in 1929, which is really the event that precipitated the creation of the SEC.
So there are these large systemic market risks which affect all of us.
And having a better understanding and the language to talk about risk is really, I think, just positive overall.

So I didn’t know this, but the SEC actually oversees more than $1 trillion in security tradings in the U.S.
So that’s a bunch of different kind of equity markets, but generally we think about these as companies that have raised money in public markets.
And so there’s a significant amount of money and exchanging going on here.
And so there’s honestly a lot of risk, as we’ve seen from different market crashes in the past.

And so the SEC’s mission is really elegant.
It’s very simple and straightforward.
Number one, they want to protect investors.
Second of all, they want to maintain a fair, orderly, and efficient market.
So they don’t want somebody over here oversharing and somebody over here undersharing.
We need to have consistent sharing so that the markets can be efficient in how they look at pricing and risk.
And basically, in the end, that facilitates capital formation.
So these are the things that let us build startups or to have companies that can invest in R&D that bring the products and services or necessary things that we need to market.
So very straightforward mission.
And sometimes it gets caught up in the whole “are they regulating too much or too little” debate.
But really, when you think about it in this context, you recognize these are important things that we all need.
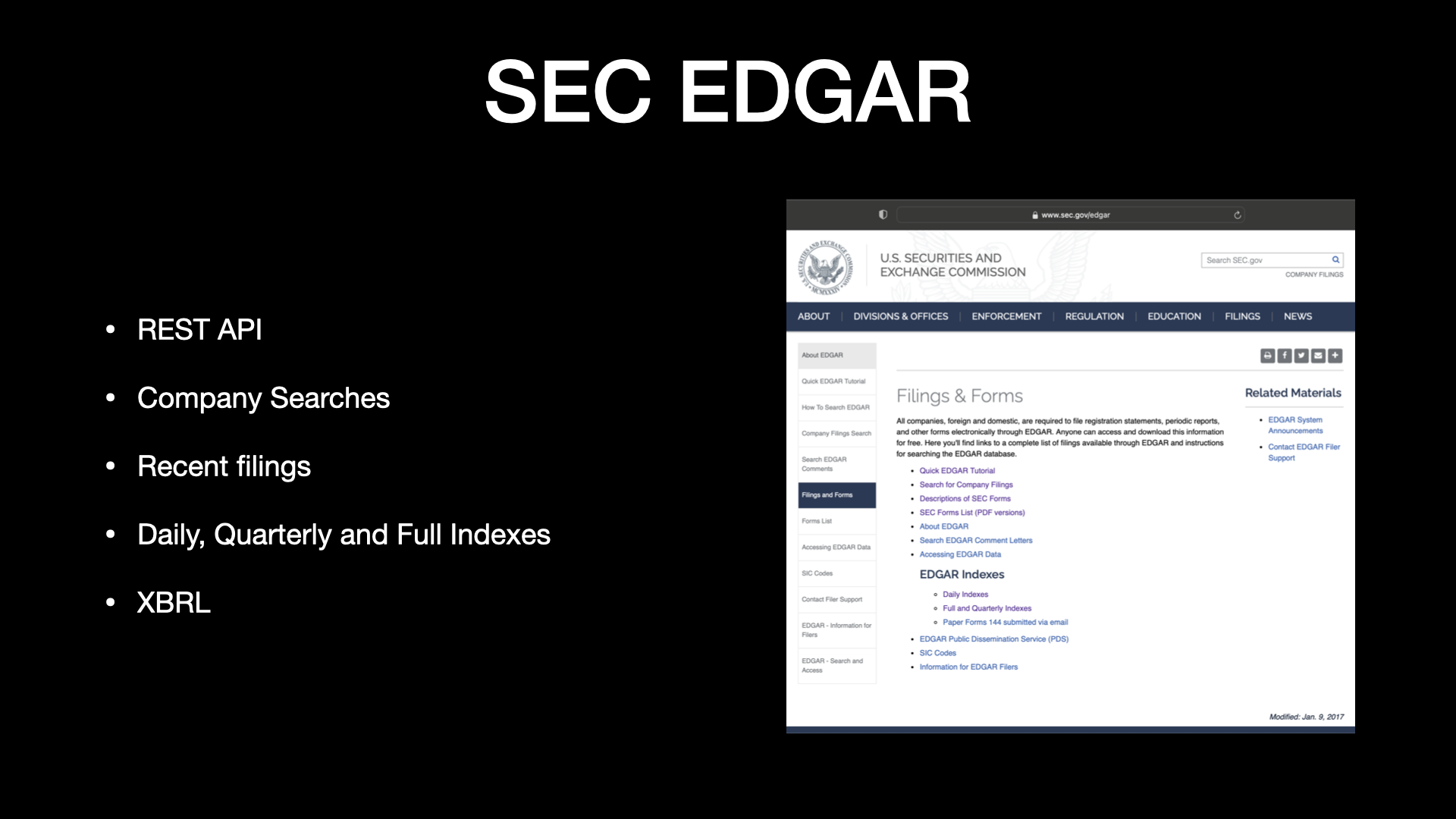
So if you get into the more technical side of it, all of the folks that raise money in the public markets, they have to submit filings.
And filings exist in a system that the SEC runs called Eger.
And there’s quite a bit of information out there.
So there’s a REST API.
You can do different company searches if you want to look up a particular company.
You can see all the most recent filings.
They actually go back and have daily, quarterly and full indexes, which is really helpful when you want to look back in time.
And then there’s a standard out there called XBRL.
So it’s kind of like XML for reporting languages.
If you think about a lot of the filings that companies do, there’s a whole bunch of accounting and financial terms in there.
And so by tagging these in a XML type language, filers can now or investors can now go out there and take a look and say, like, how many shares is outstanding at a particular company?
So if you have to go out there and parse HTML to look for that information, it’s a real nightmare.
So XBRL is kind of the technology behind that.
But the information that we’re trying to get to actually isn’t in XBRL.

And so you have to go out there and you actually have to parse the 10-Ks manually.
And as you could probably imagine, if you’re technical, that is a real pain.
I just threw up a couple of examples here.
This is something I posted a couple of weeks ago.
And basically, I assume certain things are happening in these different filings, like people follow alphabetical order.
And then you find things like item 1C comes before item 1B.
So that trips me up.
I have to write exception code.
Really wish people wouldn’t do that.
Another big annoying thing is like item gets spelled in different ways with different spaces.
This has a lot to do with how some of these companies that help filers put their information out on Eager, they have pretty complex rules where they’re automatically formatting HTML and things of that sort.
And so you get all kind of these anomalies.
And basically, it’s a real hassle.
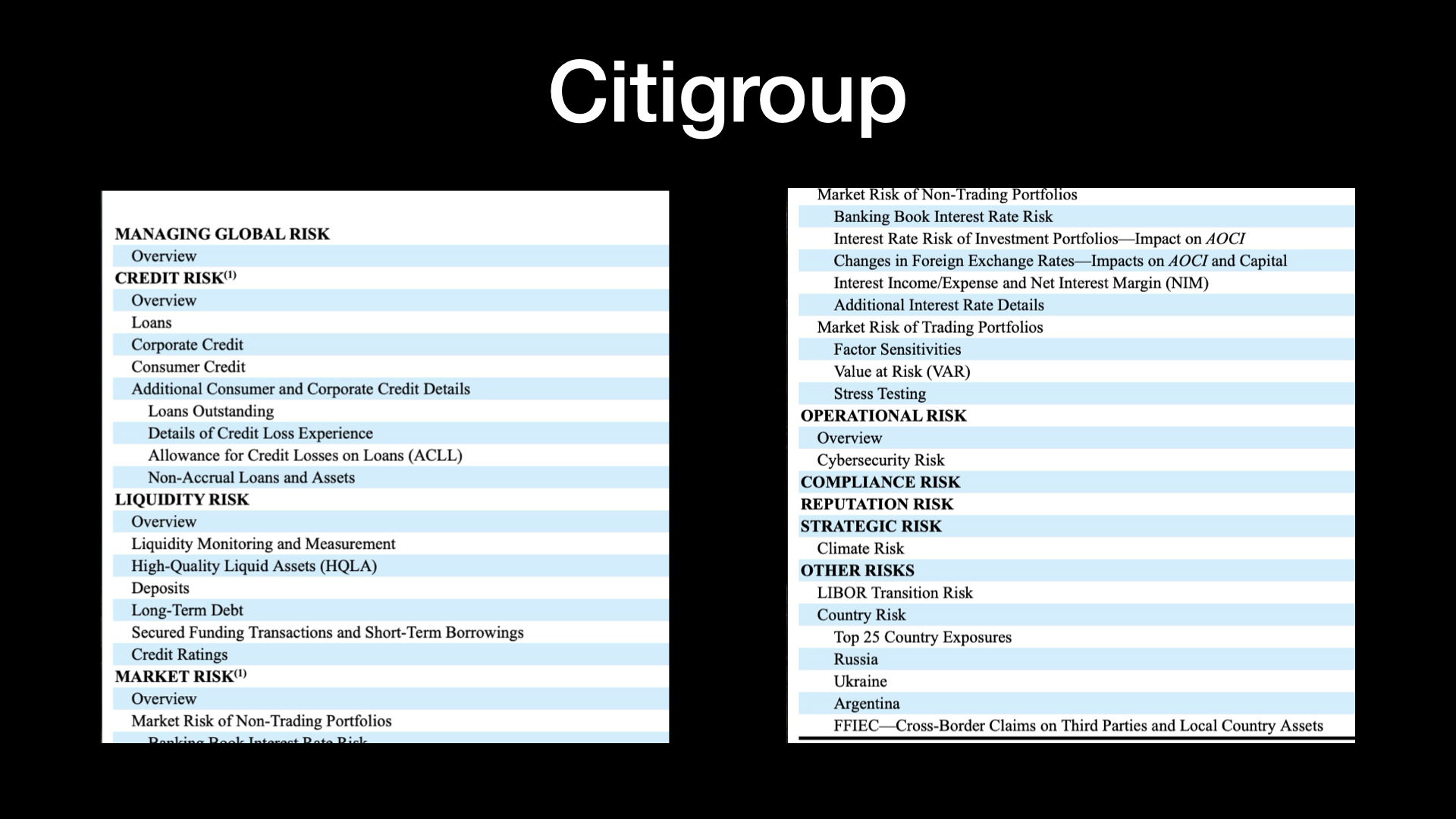
Now one of the things talking about risk that I thought I would share is, here’s an example from Citigroup that shows really a mature view of risk.
And I mean, we would expect that.
We want to see that from large financial institutions.
I’m sure some of the other large banks have something similar.
But if you go down this list, you can really see that risk isn’t just about like, well, how much money did we lose?
They have credit risk and liquidity risk, obviously, overall market risk.
Operational risk is where they put cybersecurity.
And I haven’t had a chance to look back at their previous 10-Ks to see whether or not cybersecurity risk was a line item.
But I think the fact that we’re seeing it here in their overall list of risks is really, really important.
And that was one of the objectives of the SEC in the new rules in the first place.
But when you take a look at this, I mean, they even include things like strategic risk with climate or other risks like particular countries looking at the different conflicts that are happening with Russia and the Ukraine, et cetera.
So not all of us should be here.
But it’s great because this information is out there.
And it can be really helpful to understanding kind of this risk framework.
New Cybersecurity Rules Overview
![[New] Cybersecurity Disclosure Rules](/blog/2024-03-13-impact-of-new-sec-cybersecurity-rules-snowfroc-2024/slides/cybersecurity-disclosures-snowfroc-2024.008.png)
So I want to talk about the new cybersecurity disclosure rules.
And I kind of put new in brackets here because actually the SEC has provided guidance multiple times.
First of all, staff provided guidance in 2011 and then the actual commission themselves provided guidance in 2018.
And in the press releases and different write ups that the SEC did, they said that they saw improvements in cybersecurity disclosure practices after those different guidances.
But they were still pretty inconsistent in the market.
And so if you think back to their mission, trying to have efficient, fair markets, they decided to go out there and create new disclosure rules.
And so they proposed those in March of 2022 and then they became active in December of 2023.

In their write up, they did talk about a number of trends.
And I thought the trends were actually pretty interesting, very succinct way to think about it.
So there were three trends that they mentioned that were driving these new rules.
The first one was that there’s an ever increasing share of economic activity.
So the first one is just the fact that so much of our economic activity is dependent on electronic systems.
And little tongue in cheek, I went ahead and said mobile apps.
But if you think about it, so much of what we do today is actually driven off of mobile as well.
Now the other thing is that there’s been a big rise in cybersecurity incidents.
Some of the things that they said was COVID and work from home was driving that.
But things like ransomware, crypto markets, the availability of data on the dark web, there’s really been a rise in the prevalence.
And so these have had costs and adverse consequences on companies and candidly on the market as whole.
So some things like the ransomware payments, they’re really getting out of control and they’re having significant impact on companies and on the market.
So when the SEC looked at this, they really decided that, look, we need to put in rules so that there’s consistent reporting across the board from companies so that investors have the information they have to properly price companies in stock based on the different risks that they all face.

So this is a really nice summary.
It’s taken from their document where they launched the new rules.
And I’m going to kind of take you through what the actual requirements are and then touch on some of the dates.
So on the 10-K, which are the two items at the top, there are two sections that a company has to fill in.
So first of all, they have to talk about their risk management and their strategy.
And one of the things the SEC says is, if any.
So some companies may go out there and say, actually, we don’t have any risk management and strategy right now because maybe they haven’t thought about it or maybe they don’t think they need to.
So the SEC isn’t saying you have to do this, but they’re saying that you must describe the process that you use to assess, to identify, to manage that risk, and to really identify like whether or not risks can have a material impact on their business strategy, on the result of operations, their financial conditions.
So that’s under the risk management side of 10-K.
Then there’s a governance piece.
And so governance is thinking about the board and who has ultimate oversight over management.
So who on the board is doing that?
Like what committee does cybersecurity report into and is responsible?
Because board directors have a fiduciary responsibility to the investors to make sure that they’re accounting for these risks and giving proper guidance and funding and direction to make sure that these risks have been minimized as much as possible.
So you’ve got to describe the board’s oversight of risk and then talk about management’s role in assessing that.
So that’s where we’ll end up seeing things like do folks have a CISO and how are they managing cybersecurity threats overall?
So that’s on the 10-K.
So this is done on a yearly basis.
And it’s basically the annual report where they describe what they do and what all their risks are.
So this is that new section, item 1C, that will pop up in the 10-K.
Now the other side of it is if somebody has a cybersecurity incident.
So there’s this form that’s called an 8-K.
Companies can file 8-Ks.
In fact, they do it all the time.
And this is where they need to disclose something material to the market.
In this particular case, the SEC said, hey, if you have a cybersecurity incident that you think is material or maybe material, then you need to file that within four days of determining that it could be or may likely be material.
Now that four day actually has a carve out.
So if, let’s say, you’re a company that does work for the federal government or Department of Defense and there’s a national security carve out, you can go to your local FBI office and they will literally have to go to the attorney general and get a basically a disclosure from them saying, hey, you can hold off for now and delay.
But it has to go all the way up to the attorney general.
So the bar is set really high.
A couple of things to note here.
The 8-K, you need to talk about the nature and scope and timing of the incident, but also the impact or reasonably likely impact.
The other key thing is that if you don’t have all the information, that’s fine.
It’s not expected that you would.
But after you have new information that you determine is material, then you have four business days again to file that update.
So the timing for all of these is the 10-K item 1C affects all registrants and it’s based on their fiscal year end.
So if they have a fiscal year end on or after December 15th, 2023, then when they file that report, they need to have an item 1C.
You’ll find some of the ones out on my website will basically say not applicable.
Apple’s a great one because their fiscal year end was I think sometime in September.
So basically some people get a pass this year, but most people are going to have to file.
On the 8-K item 105, the material cybersecurity incident, that became effective December 18th.
But if you’re a small reporting company, you actually have another six months before you have to start reporting.
And then both of them need to include XBRL tagging within about a year.
So December 15th, 2024 for 10-Ks and then December 18th for the 8-K.

So materiality or is it a material incident?
This is a really important word and there’s actually been quite a bit of discussion to date on LinkedIn about this.
So why did the SEC choose this?
So first of all, they actually talked about this in their press release and their discussion.
So first of all, we all know that companies are attacked on a daily basis and we don’t want people going out there and posting every single attack they have because that’s not material to an investor’s decision or a reasonable investor’s decision about would it necessarily impact the company.
So it’s like the attack has to actually rise to a certain level.
The other really big thing about materiality is it connects back to a whole host of litigation to regulatory to powers that the SEC has been given by Congress.
So materiality means something.
It is a defined thing.
Justice Thurgood talked about it.
It’s been litigated multiple times.
So materiality is this really important mark that says a reasonable investor would want to know whether or not this has taken place as they evaluate essentially the value of your stock, the value of your company.
And so I think the good news of all of this is that cybersecurity is now considered a true risk and there is a marker for saying this is material.
And if you’ve been in cybersecurity for a long time, we’ve all been waiting for this moment.
So this is actually a great moment because it’s going to drive transparency and visibility to cybersecurity and really help us put in place the resources, the risk management, the strategy that we need to protect companies and candidly to protect our country because so much of what we do is at risk when we have intellectual property theft, when we have identity theft and so much of the information about US citizens is taken.
So this is really in my opinion not just an issue about the price of a stock and things of that sort but it actually is much, much broader in terms of overall national security.
Recent 8-K Disclosures
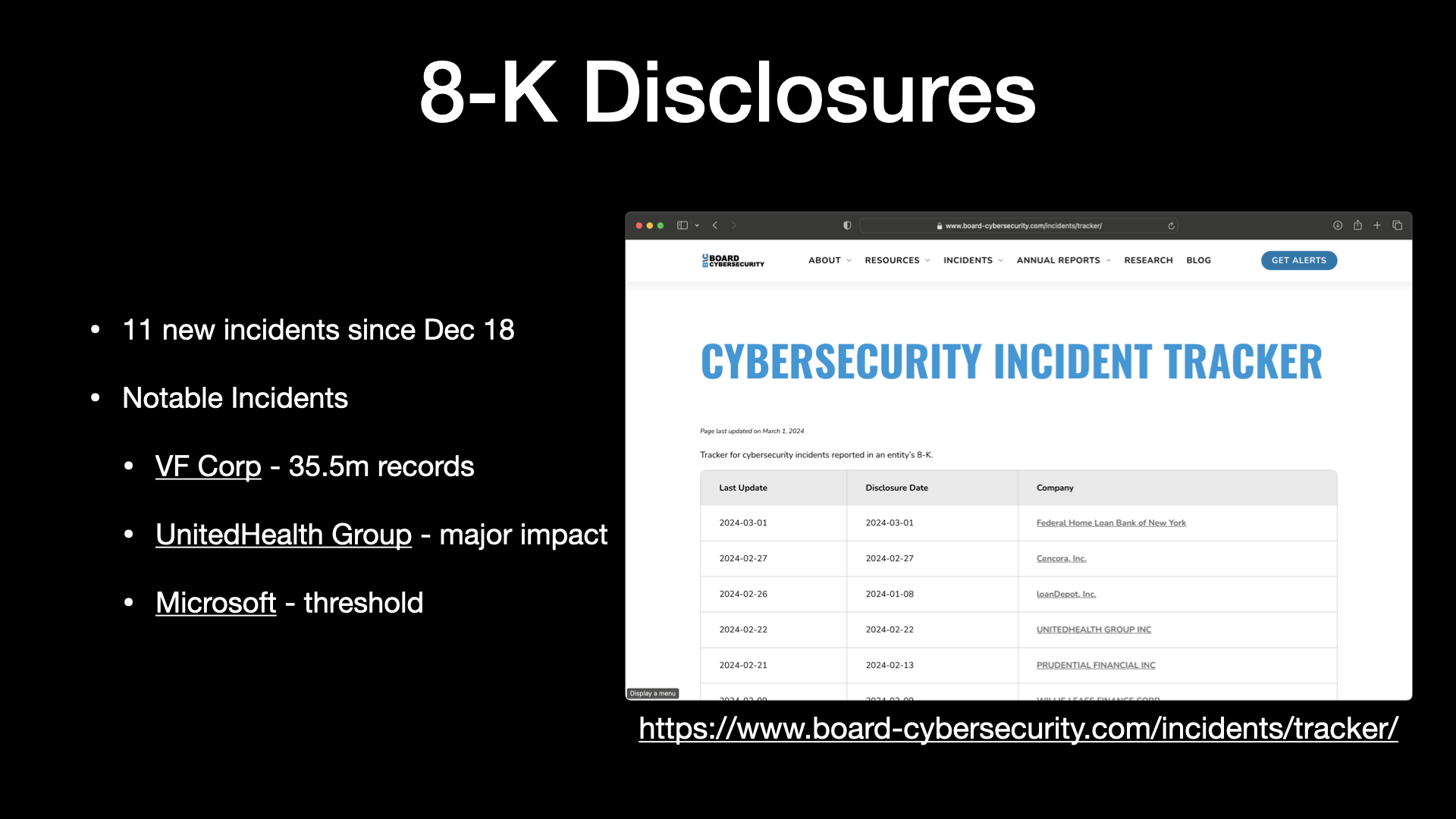
So I created a cybersecurity incident tracker.
It was the first thing that I worked on.
And basically every five minutes I go out, my script checks the SEC website, I download any new 8-Ks and then I use some tagging and some keyword searching to try to determine whether or not it’s an incident.
Since December 18th, there’s been 11 incidents.
That’s as of last week, I think maybe a new one came out or two since then.
So there hasn’t been a bunch but there certainly have been noticeable amount.
And I call out a few of them here.
So VF Corp was a breach that’s affected 35 and a half million people.
United Health Group is probably one everybody’s aware of.
They’re having a major impact now.
I think probably affecting about a third of the United States prescriptions out there.
So it’s a significant incident.
And then Microsoft has been in the news lately because they had an email compromise that really is starting to get more and more unraveled about what’s going on there.
What are the overall potential risks coming in from like a nation state attacker?
So I’m going to take you through a few of these live real quick just so you can see them.
So you can go out to board-cybersecurity.com.
So I’ve got the incident tracker out here.
And again, you can see that, you know, here’s the different incidents.
And as I mentioned, since I’m recording this about a week later, there have been a few updates.
Companies have to post updates as we talked about earlier if there’s new information.
So United Health Group and Microsoft have posted different updates since my last talk.
But you can come in here and, for example, take a look at VF Corp.
You can see a little summary about the company, details about the incident as we become aware of them.
So the 35 million records, tracking different dates here.
I think it’s really interesting to look at a compromised date versus when it was detected, disclosed, contained, and recovered.
And then looking at different attacker goals and cost track.
Now there’s a lot of kind of data entry and reading that has to go on here.
If you’re interested in this topic and want to consider being a contributor, there’s lots of different ways to help.
I have a contributor section here so you can take a look at how to contribute.
And one of them would be just kind of keeping up with all of these different filings and the different data points.
So I go out there and I post the actual incident and all the details here so folks can come in and take a look at that.
And then I also track different analyst notes and news articles out there.
And so this one was really interesting.
After VF Corporation submitted their incident, a few days later the SEC reached out to them and said, “Hey, great.
Appreciate you posting this.
It looks like you didn’t include all of the impacts to your company and we know that you’re going to update that in the future with an amended 8-K.
So when you do that, don’t forget to consider some of your material impacts here, things like these qualitative metrics.
So it’s not just about impact to the bottom line, immediate impact of cost, things like vendor relationships and potential reputational harm.
So the SEC is really trying to get companies to think about risk, not just in kind of an accounting and kind of a first order impact, but really getting to that second order and third order impacts where you would say litigation, reputational impact, long-term recurring costs, new investments you had to make.
These are all things that a reasonable investor would want to know.
As I mentioned, United Health Group and Change Healthcare has been a really big one out there.
So this is an example where you can see tracking also different related articles.
So it helps kind of keep up to date with what’s going on there.
And then Microsoft, as we mentioned earlier, they just posted a brand new update.
We have four of the key dates here so we can see when they were compromised, how long the attackers were in their infrastructure, which, you know, that’s actually quite a bit of time from November 27th to the 12th when it was detected.
And then they disclosed on the 19th and Microsoft believes they contained it on the 13th.
Now what’s interesting is if you take a look at the update that they just posted, I think yesterday, they basically say that there’s an ongoing sustained attack that they are experiencing as a result of this information.
So you know, maybe it was contained as of 1/13, maybe we’ll find that it wasn’t.
So this is what the incident, Cybersecurity Incident Tracker looks like.
And if you’re interested in getting alerts, all of these pages actually have a RSS feed in them.
So if you’re on the techie side and you just type in index.xml, you’ll get an RSS feed.
You can also just click get alerts here.
And then when a new incident comes out, or if you sign up for the incident updates, or occasionally, I’ve never done this, but sending out some news and updates about the site, you can sign up here and then I will send you an email, usually pretty quickly after a new incident or incident update posts.
So that’s kind of the 8-K disclosures.
Cybersecurity Incident Reports
Now one of the things that I realized is we’ve been spending a lot of time trying to think about what is a material incident.
And so we can go out there and say like, well, if a company filed a item 105 in their 8-K, then we know it’s a material incident.
But it’s actually a little bit more difficult than that.
A lot of the companies filings say we haven’t yet determined if this is material.
I think to date, only one of them has said, hey, this is material for a quarter, but we don’t think it’s material after that.
And again, I think a lot of these companies are thinking about it strictly from a financial impact standpoint.
And so I think over time, the SEC is really going to push them to think more broadly about that.
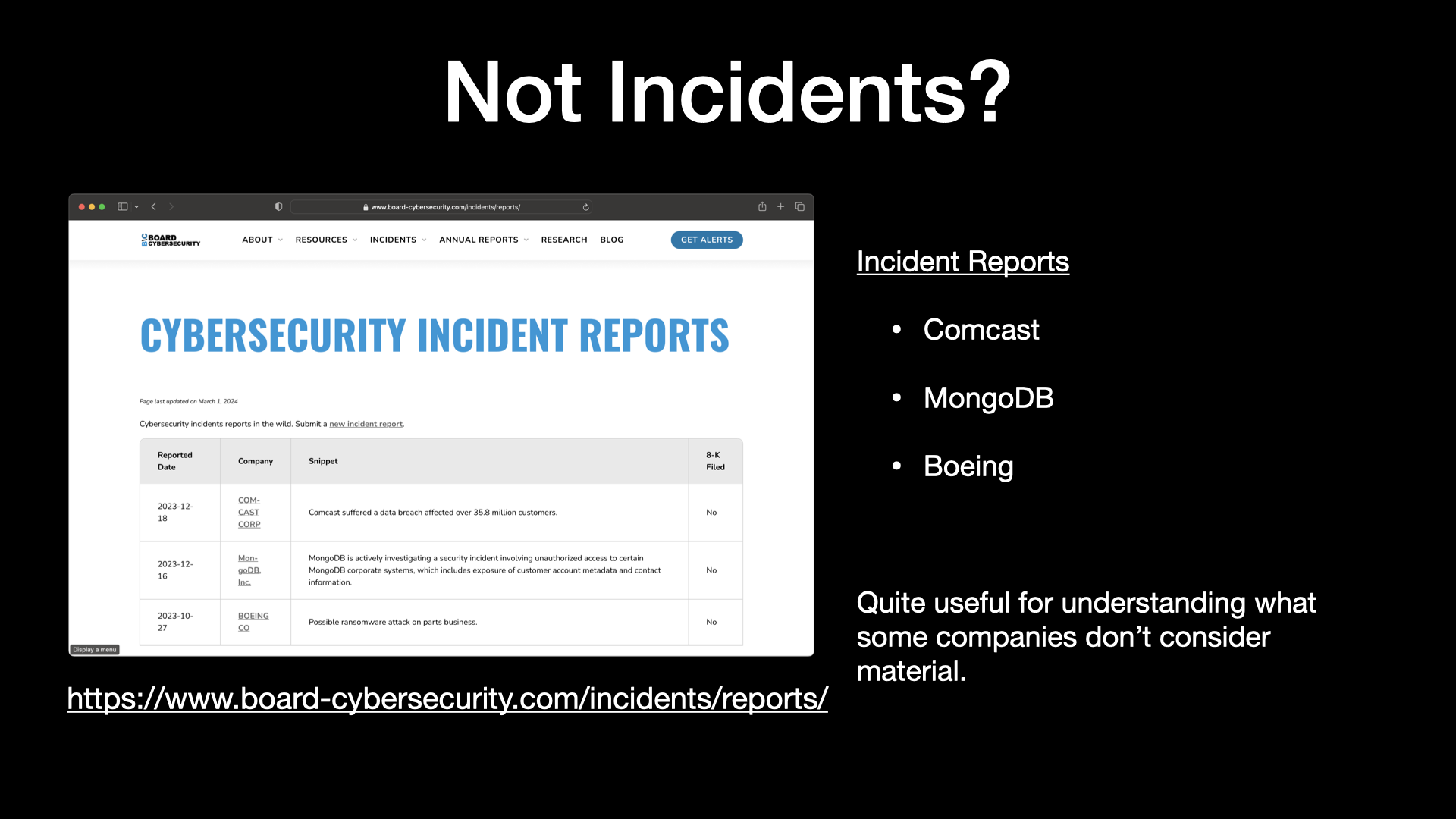
So one of the things that I thought was interesting is, well, what if we track basically incident reports?
Maybe it’s news, maybe the company’s confirmed it, maybe we find something on an attorney general breach website and track those and say, OK, Comcast had a data breach from Citrix, from the Citrix vulnerability.
There was over 35.8 million customers impacted.
And to track whether or not there was actually an 8-K.
So to date, we haven’t seen an 8-K from Comcast.
So we can infer that in their mind, this is not a material event.
So I think that’s super interesting.
If you click out to incident reports, so you can come up here, you’ve got the tracker and then you have incident reports.
You can see the list here.
And so actually one came out yesterday.
And so again, this site has been updated.
So Roku has had an incident where a little over 15,000 people have been impacted.
The attorney general websites are fantastic.
I link out to that.
So you can actually come out here and see it was 15,363.
This one’s really interesting because the date of the breach occurring was December 28th, 2023 to February 21st, 2024.
But they’ve discovered it not on a single day, but nearly seven weeks.
So I’m not really sure what to make of that.
I just find it to be an interesting data point.
So you can come out here and see these different incident reports.
And then should these ever be converted into an actual 8-K incident, then I’m going to go ahead and update that so that we can see like, okay, this one went from an incident report to an actual 8-K incident.
I track a lot of InfoSec news, so hopefully I will catch these.
But if you’re ever out there and say, hey, you want to get in touch with me, you can just click the new incident report here or connect with me on LinkedIn.
Let me know and I’ll take a look and hopefully get it posted out here on the cybersecurity incident reports page.
So and then I have a few others out there, Mongo, Boeing, et cetera.
8-K Observations

So I want to talk a little bit about 8-K observations now.
I follow quite a few folks on LinkedIn. Ezra Ortiz is one of them. He’s been actually doing some really great work going through different 8-Ks and 10-Ks and just doing some analysis on them.
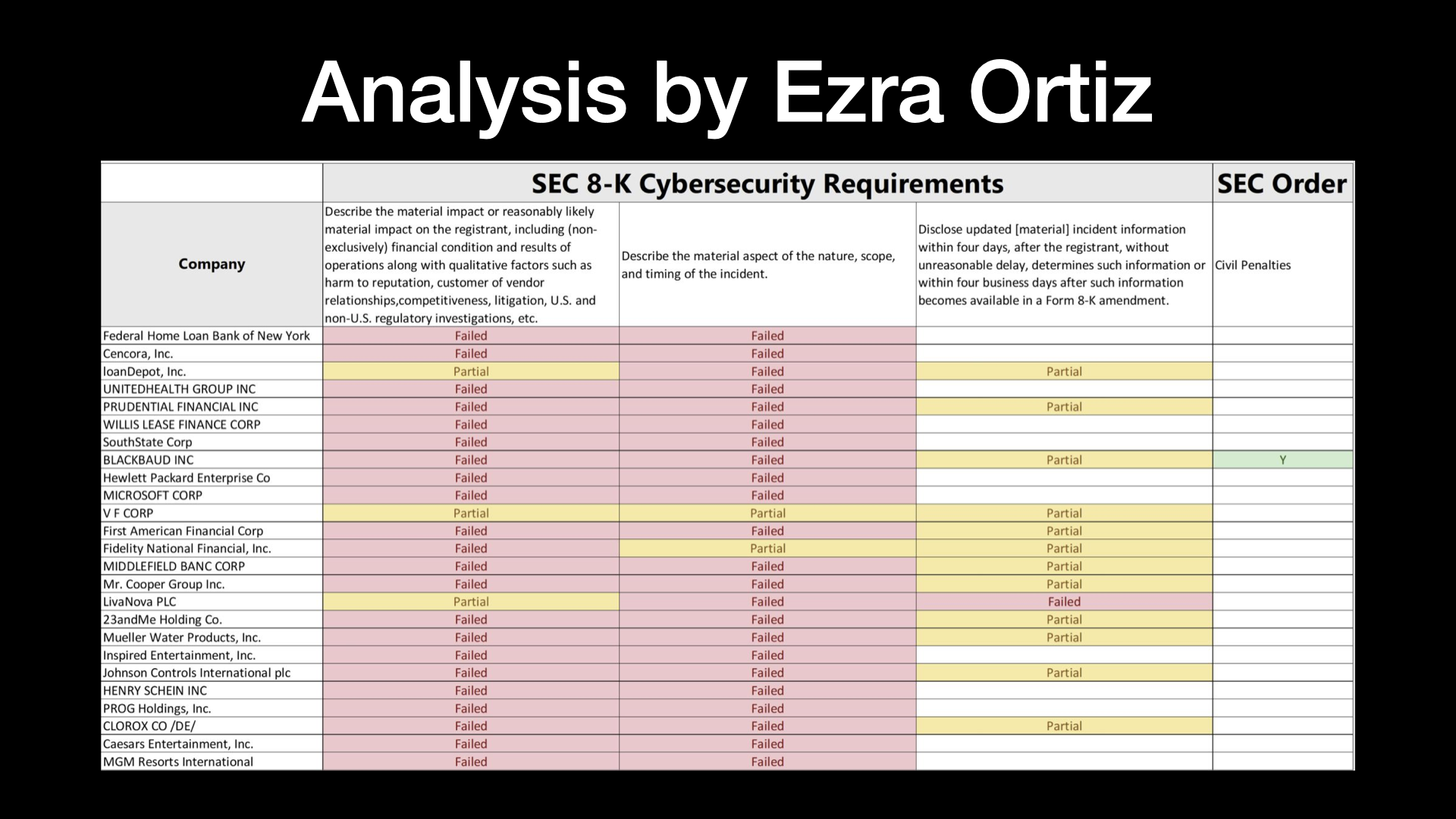
So he provided this analysis in a LinkedIn post.
This is a link here, so you can click on it.
I’ll make my slides available.
So you can go out there and take a look at his post.
But basically he went through and said, OK, the SEC has these different requirements for an 8-K disclosure.
And basically this is his thoughts on how effective the companies are doing in terms of complying with the requirements.
And as you can tell, you know, from Ezra’s standpoint, not very good.
Now, I didn’t really pay attention during Sarbanes-Oxley and, you know, after the Enron fashion, everything kind of came out.
And so my suspicion is that companies are trying to figure this out.
The SEC is trying to figure this out.
They’ll be using correspondence and conversations with companies.
Companies will be looking at each other and seeing what folks do.
And it’s just going to take a little bit of time to get into a much better reporting standard here.
So this doesn’t surprise me, but I think directionally Ezra’s analysis is accurate.
A lot of these are really not complying with the rules that the SEC has put out there.

So some other observations.
There’s actually a lot of data in them.
I mean, my first reaction when I started reading 8-Ks was, wow, this is really lawyered up.
It’s very, very carefully worded.
But if you read closely, like you’ll find really interesting dates, dates that maybe you don’t get in the first posting, but you get in a later posting, or you find it in an attorney general posting somewhere.
So if you follow this over time and we kind of do a look back, there’s actually some really great information that we’ll end up finding.
So the dates are a really great way to think about this.
One of the ones on the website that has the most information is Blackbaud, because they were actually compromised I think in 2020, maybe 2021.
There’s been a bunch of litigation.
The SEC has fined them.
And then I think recently the FTC did.
And if you read the FTC report, there’s a whole bunch of information in there.
So we get a peek into the inside that we don’t normally get.
So great information out there.
Another trend that’s been interesting is that we’re increasingly seeing nation state actors mention.
So United Health Group, Microsoft, HP Enterprises mentioned this.
So it’s just a new trend that I’ve noticed.
Instead of just being an attacker, we’re increasingly seeing companies talk about nation state actors as the perpetrators behind these attacks.
And as I kind of showed you earlier and already mentioned, the state attorney general breach websites.
And I really like Maine’s website because they have a lot of detailed information out there.
But there’s quite a few states now that require, they require notification if more than some number, I think in Maine it’s literally two, people are breached in their state.
And they put some just really great information out there, not just in the summary that you saw earlier about Roku, but you can go look at the sample breach letter.
And that’s where I’m able to get like detailed information on which data points, you know, what data has been breached and exfiltrated.
The SEC doesn’t require a company to share that, but because the attorney generals do, you know, we can kind of piece these things together.
10-K Analysis

Okay, switching over to 10-Ks.
So as of my talk last week, I had, you know, 2359 10-Ks.
And these literally get updated to the tune of tens or hundreds a day.
I have a script that runs automatically, usually every hour.
It’ll grab the most recent batch and then it’ll push them out there.
So I do skip some of them when I do the analysis for low word count.
There’s a whole host of 10-Ks that I mentioned where they’ll basically say not applicable.
And this is because their fiscal year end was before December 15th.
And then even though I’ve significantly improved my algorithm for extracting information, I still have about 5% of these or 125 of them right now, where I wasn’t able to extract the item 1C automatically.
And some of them are like really complex filings, like from banks, where they don’t just do like a table of contents and here’s your cybersecurity section.
They actually do like a significant document with an index that does a cross reference to the lookup.
And so at this time, like it just isn’t working from a parsing standpoint.
And so I just kind of treat those as one off.
I did try to run them through ChatGPT and was hoping kind of like a large language model might help.
It started hallucinating by the third one.
The context windows on these documents are so massive that it’s just really probably going to take some sort of local LLM or specialized NLP running.
And so now it’s really more just fine tuning my extraction script and then dealing with these exceptions one off.

Now one of the things I did think was interesting was just kind of looking at word counts.
And you know, word counts, is that interesting?
I mean, you can’t really say that’s a proxy for quality, but it at least tells us something.
And so I kind of did a 5/50/95 analysis.
And so at that time, you know, you can kind of look at this and I have a chart I think coming up here where, you know, a lot of them were sitting out in about 700ish words.
But as you push out, we’ll get into the 1500 or over 2500 word count.
So there’s just kind of an interesting analysis we can do here with percentiles.
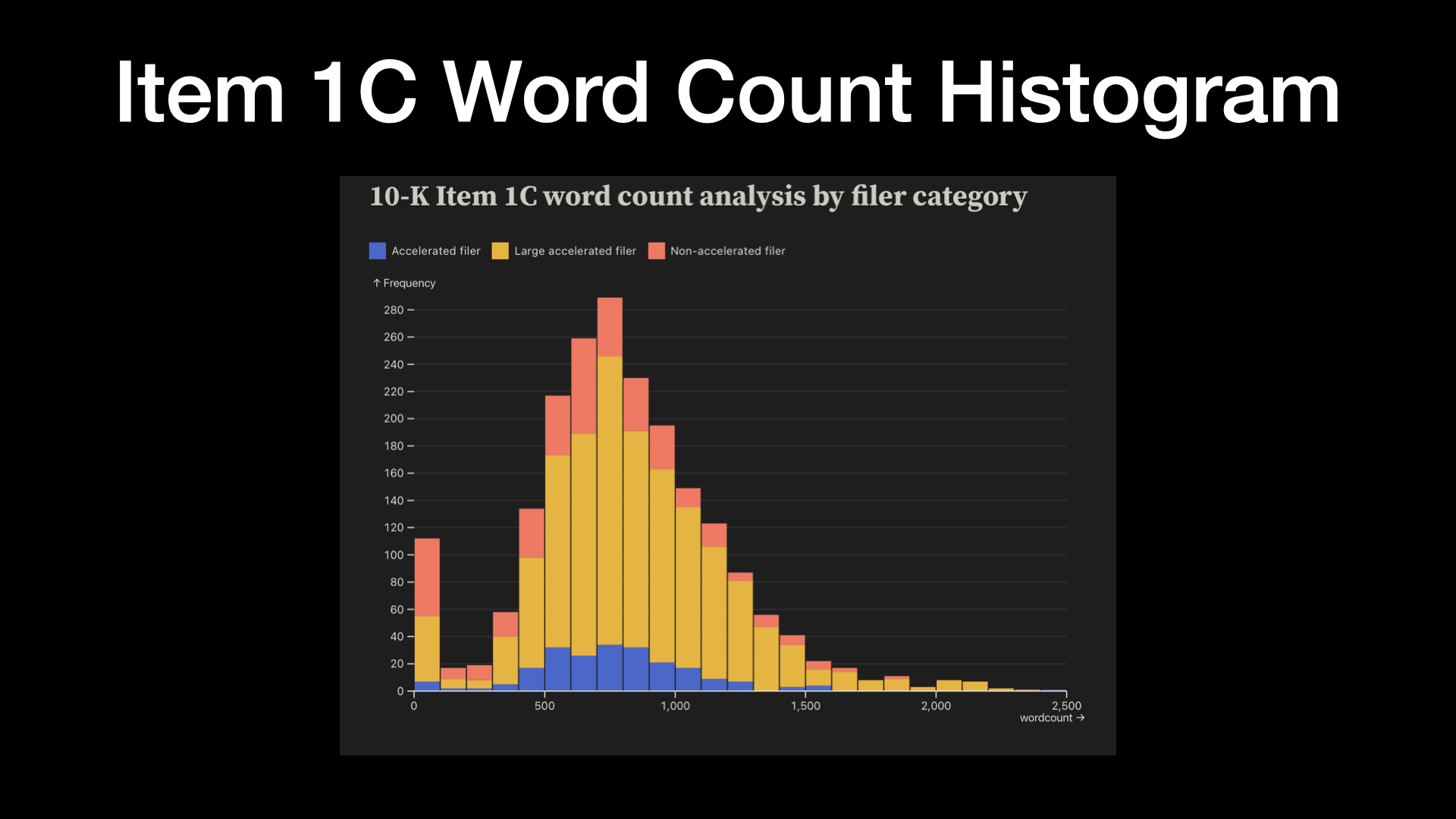
And here it is, next slide.
Prettiest slide that I’ve ever made.
Shout out to Observable Framework.
Really, really cool.
These are the folks that bring D3.js.
It’s been around for a long time.
But basically you can do some amazing charting and graphing.
You can post this stuff statically on a static website.
So I do intend to post these out on the website soon.
But you know, just kind of looking at the word count here, you can see that predominantly we’ve got, you know, almost a bell curve here except for the folks that are on the end of having no information extracted, which I probably should have excluded.
And you can kind of tell that like the large accelerated filers, so the biggest companies out there, those are the ones in yellow.
Those are the ones that as you go further out to see the higher word counts, you’re almost exclusively going to get these large, sophisticated organizations.
So accelerated filers are kind of in the middle and the non-accelerated are the smallest ones.
So just a little bit of interesting analysis on word count.
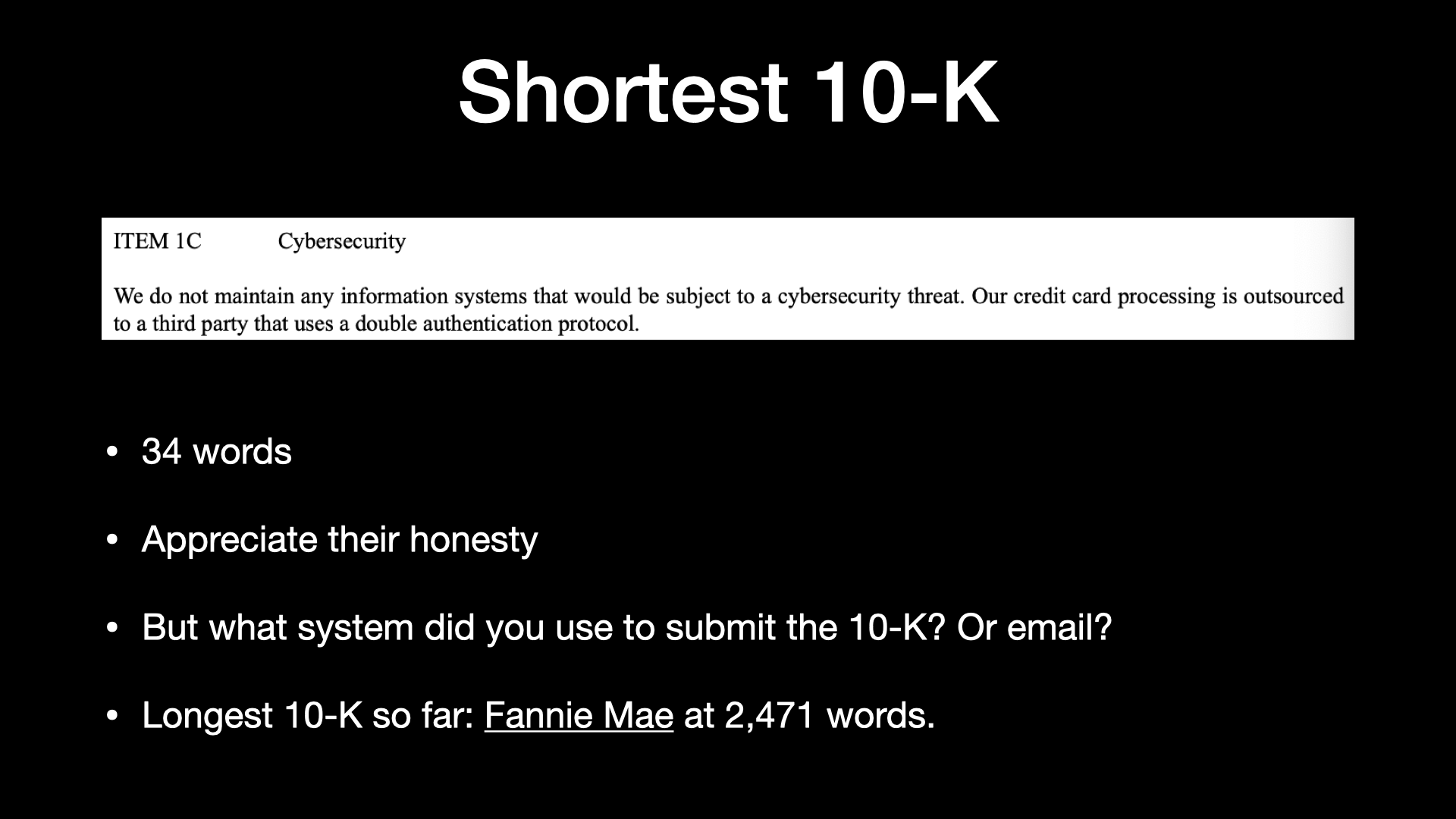
So in case you’re curious, shortest word count, I’m not going to say who it was, but I thought it was really interesting, right?
It’s 34 words long.
It says, “We do not maintain any information systems that would be subject to a cybersecurity threat.
Our credit card processing is outsourced to a third party that uses a double authentication protocol.”
So one, appreciate their honesty.
Two, you wrote this on something or had somebody write it, you probably use email.
Phishing is still a major way that people get attacked.
There’s probably information in your email.
So I don’t fully agree with it.
I do think some sort of cybersecurity risk management that would be appropriate for their company should be in place.
But again, that was the intention here, like share what you have in place.
And for all you security people out there doing MFA, you’re obviously doing it wrong.
You need to do double authentication protocol.
I’d say the other big, the interesting one was just like the largest one to date is Fannie Mae.
And so they’re coming in just under 2,500 words.
So now I’m actually going to pop out and do some live analysis.
To see the analysis, please check out the YouTube version of this presentation.
And again, this is using the observable framework, which I do hope to publish out on the web.
These are really pretty and they’re like, they’re about penguins and things.
So I just kept them on there because it was a nice graphic.
So the things that I’ve done over here, we’ve already seen the item 1C word count.
But I did some really basic analysis.
I’ll take you through them real quick.
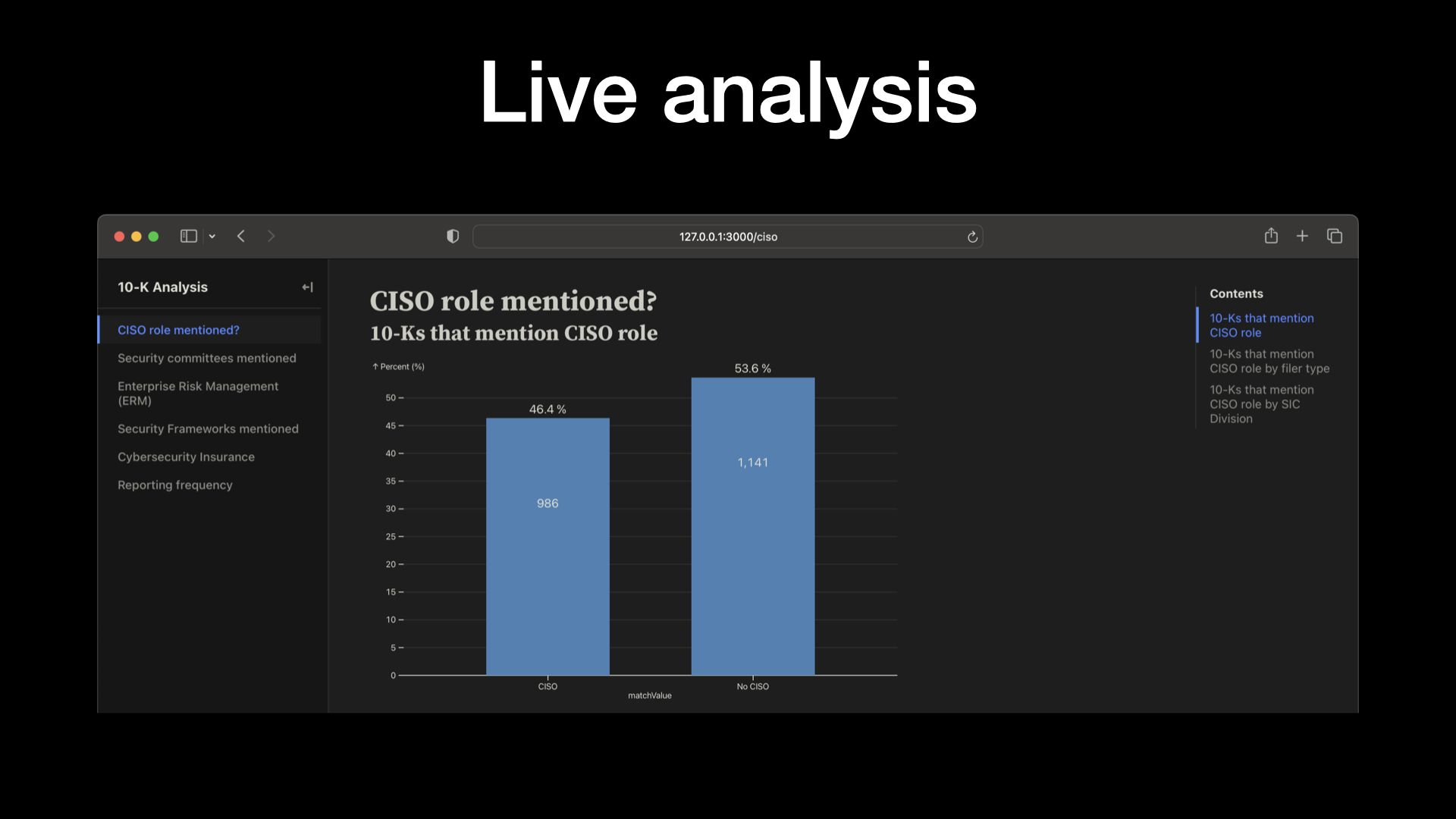
So first of all, like is a CISO role mentioned?
Right now these are point in time and I intend to do kind of like trends over time.
But 43, 44% of the companies mention a CISO in their 10-K and 56% don’t.
So actually, I feel that’s a little bit low to be honest.
And you know, arguably a best practice would say you have an executive that specifically focuses on cybersecurity.
So I did CISO and CSO.
If you have ideas on additional words to include in this analysis, again, just reach out to me.
I’m not going to take you through all of the slides on all the pages here.
But just to give you a quick rundown, one of the things I do is I then kind of pivot that over different properties.
So let’s say we take a look at that role, not just overall, but by the filer type.
So large accelerated filer, the accelerated filer kind of in the middle and then the non-accelerated filer.
And so not surprisingly, the large accelerated filers tend to have a higher percentage of naming a CISO.
So that makes sense.
And you can kind of see that drop off, you know, actually pretty significantly as you move into the midsize and smaller companies.
And then the SEC still uses SIC.
They haven’t moved to any ICS.
And so I tried to group these a little bit.
I need to do a little bit better on the groupings.
But it’s interesting to just kind of look at by group.
So for example, the services companies actually do the best with over almost 61, 62 percent name a CISO or CSO.
I actually would have loved to see this category a little bit higher.
So this is basically financial insurance, et cetera, so banks.
But this is kind of the breakdown.
Forestry and fishing is doing pretty good, but it’s only four filings.
So OK, not quite as interesting.
And then you come all the way down here to mining.
And so less than 20 or right around 20 percent of mining companies have named a CISO or security executive.
So security committees mentioned.
So where does cybersecurity report into?
So in a really simple analysis, pretty much 85 percent, almost everybody mentions committees.
And overwhelmingly, and it’s going to be hard for you guys to see this.
I have a better analysis I’m working on that will group these into two bigger categories.
But a very significant percentage are reporting into the audit committee.
You’ve got 68 percent here, but honestly, you’ve got a bunch of them down here.
So probably more like 75 percent plus are reporting into an audit committee, which on one hand, I think is pretty good because the audit committee is powerful.
You typically have the CFO on it, the CEO.
But at the same time, the audit committee is also looking at internal and external audit.
They’re looking at compliance issues, oftentimes legal.
So there’s a lot going on in the audit committee.
And the big fear would be that you just get a little bit of time for a security conversation.
Enterprise risk management, as I mentioned earlier, this really kind of kicked everything off for me.
And so from an enterprise risk management standpoint, the about 55 percent of the companies mention ERM.
I think that’s really good.
So this is thinking about risk broadly across your organization.
And then now, including cybersecurity is one of those risks that’s being tracked.
But still, about 45 percent don’t do that.
And you can just again see a breakdown where not surprisingly, our larger companies tend to have enterprise risk management programs in place.
A little bit more near and dear to my heart from a security practitioner are the frameworks themselves.
Nearly half of the people are just over half do not name a specific framework.
So I think that’s room for improvement.
Don’t roll your own crypto and don’t roll your own security framework.
Just use things that are out there.
I have some better analysis coming out here soon where I group them again better.
But the majority of what I’m seeing out there is the NIST cybersecurity framework.
Version two just came out.
It hadn’t been updated for 10 or 11 years.
They now have a governance category.
And so I think, you know, taking a look at cybersecurity framework is probably a really great idea.
I suspect that we’re going to predominantly see this one take off.
You will have things like NIST 800-53.
Let’s say for people that do a lot of work with the federal government.
We see ISO 27001 coming in around 8 percent, CIS around 4 percent, and then COVID, COSO and whatnot are just kind of don’t really show up.
I thought it would be interesting to take a look at cybersecurity insurance.
Basically not really mentioned much in 10-Ks.
And, you know, again, I’m not much of an insurance guy, but insurance is a really interesting way to kind of transfer some of your cybersecurity risk.
So this would be a category that I’m watching closely over time to kind of see, you know, how much do we end up seeing cybersecurity insurance being a part of a risk management strategy that companies employ to manage overall risk.
And then lastly, and I’m not sure the keyword search here are perfect, but I think it’ll give us some directional ideas.
What we really want to see is like, what is the reporting frequency?
Are cybersecurity professionals or executives reporting to the board regularly or as needed?
Or is it quarterly or annually?
So did a little bit of searching on that based off of keywords.
And you can see that a fair number of folks mention quarterly or annually.
And you know, quarterly is slightly higher.
Now, we could be crossing wires a little bit.
You know, maybe they’re talking about some other quarterly event that takes place.
So there’s some work to be done on this analysis.
But I think just generally thinking through like consistent reporting frequency and then going out there and measuring on that is important.

OK, so I’m going to wrap up this talk with best practices.
So I’m going to take you through like the 8-Ks and the 10-Ks.

But there’s an overarching concept that I have, which is learn from these disclosures.
Like this is this is great stuff.
Companies now have to do this.
They are spending real money and more importantly, real time and energy thinking about how do we better manage cybersecurity risk.
And so if you’re a publicly traded company, if you’re a startup, if you’re in the middle, like learn from these disclosures.
If you’re like, hey, I really need to put a better program in place.
I want to use a framework.
What framework should I use?
You should probably use the NIST cybersecurity framework.
I mean, certainly, you know, CMMC and other ones are going to come into account. 800-53 if you’re in the federal space.
But by and large, you know, go out there.
That’s a kind of middle of the bell curve.
Best practice, just, you know, go out there and look at these different filings and learn from them and then adapt and use them for your for your company.
8-K Best Practices

So 8-K best practices.

First of all, define materiality in advance.
Make sure that you’re including both qualitative and quantitative factors.
So not just like, hey, here’s the here’s what we had to pay out in a ransom or hopefully you didn’t have to pay out a ransom or here’s what we paid for cybersecurity experts.
But think about those other impacts to reputation on supply chain.
And that’s really hard to think about because, again, this is kind of second order and third order thinking.
And it’s hard for us to do that.
But I think if we really want to understand and quantify the impact and cost of cybersecurity risk, you have to get past these kind of knee jerk, quantitative, kind of really easy to figure out.
It’s it’s a number, right?
You may not know day one, but it’s a number and you’re going to be able to figure that out.
So you both.

Second of all, don’t forget that you have to talk about reasonably likely impact.
So this gets overlooked a lot in 8-Ks.
And so let’s just say you had a major breach in terms of records impacted.
Is it reasonably likely that you may have a class action lawsuit?
Probably.
I mean, even on the Roku event, which came out, I think one day ago or two days ago, you know, if you got to read it to the world or whatever, people are already talking about that.
So if you and me had a breach, they clearly have class action lawsuits coming out at them.
So you have to think about reasonably likely impacts and make sure that you’re including them because to date they’re being overlooked.
When you have new information, you have to post an amended 8-K.
So you’re subject to that same four day window.
It’s again, after you determine that it’s material.
But basically it’s not a one and done.
You need to keep updating the market with new information.
One of the other big things, and I think the SEC thought really hard about this, information system includes anything that is owned or used by the registrant.
So it’s not just like I have a data center.
It’s your supply chain.
If you use a SaaS provider, you know, if you use Google sheets or Microsoft’s equivalent and there’s a spreadsheet that gets compromised in the cloud, that that’s included.
So don’t overlook the supply chain.
These are squarely in scope for 8-K’s.

You want to identify your core team in advance.
So when a potential incident hits, you don’t want to be scrambling.
So basically go out there.
You’re going to have a lot of pressure in terms of legal and regulatory pressure.
So have the team in advance, figure it out.
So you know who all is going to be working on this.
And you know, kind of follows from that.

And this is something that I think security teams and IR teams are already doing really great is tabletop exercise.
Set up an incident.
Who’s on the call list?
Who’s going to make a decision about sending out a press release?
How long does it take to determine materiality?
Is your vendor that posted the 8-K if you have to do a posting there ready to go?
What about the state attorney general websites?
How are you impacted there?
So tabletop exercise this because, you know, just like when I do development, if I do something once, it’s actually pretty rough.
But by the time I do it the third time, I’ve really figured out a more elegant approach.
And that holds true for things like dealing with incident disclosures.
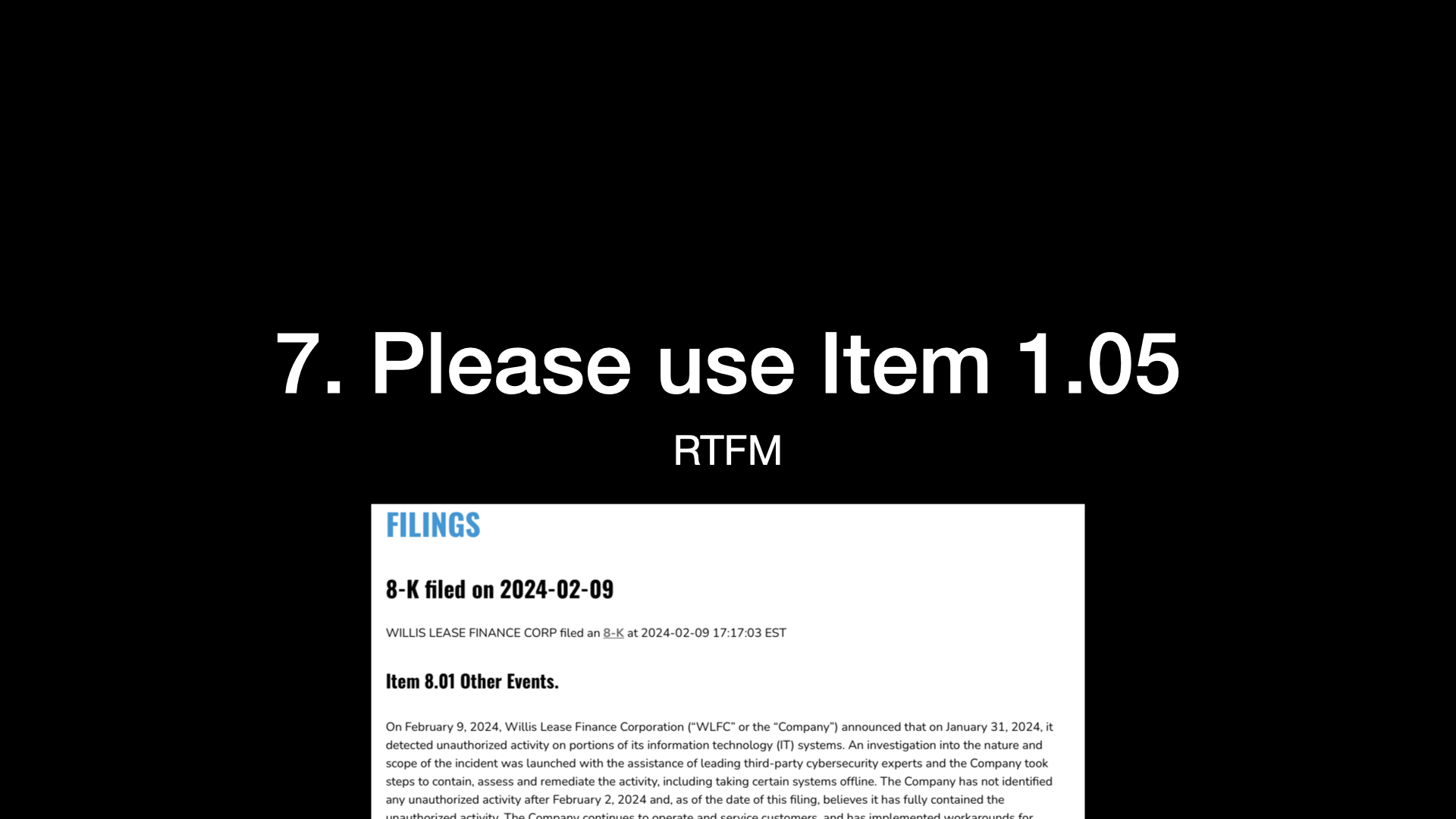
And then, you know, just a minor quip, please use item 105.
I mean, the rules came out in December 15th.
It’d be great if everybody just followed that.
There was a filing on February 9th that got filed as item 801.
Now that’s one of the older items you could have used.
Generally, they’d come in under a 701 or 801.
My script catches it.
I’ll continue to look for those in the future.
But you know, basically read the manual.
It’s out there.
It tells you exactly what you need to do.
10-K Best Practices

So on the 10-K best practices.

So first of all, I mean, it’s kind of a silly thing to say, but only state factual items.
And let me give that a little context.
Like if you go out there and say we’re compliant with NIST 800-53, we better be compliant with NIST 800-53.
And there’s a lot of things to do there.
So are you really fully compliant or do you have a team that’s working on being compliant?
Do you use 800-53 as guidance and have adapted 80% of the controls and tested and gave yourself this sort of score and you know where your gaps are, but 20% of them are not relevant and you have a two year plan to become, to close those gaps.
Like whatever it is, if you put information in there that’s not factual, then I think there’s a liability issue.
You know, should there be an incident in folks look back and say what you do, you know, and clearly we’ve seen this happen, right?
With things like solar wind and Uber.
You know, personally as a security guy, I think that CISOs are being scapegoated.
To me, this is not a CISO issue.
And a lot of times we’re not seeing CISOs, you know, reporting either, you know, to the board or working on those committees or crafting those disclosures.
There’s layers of management and executive management and attorneys and whatnot that are involved.
So you know, we shouldn’t scapegoat the security folks, but we need to be out there and really stating things that are factual so that you don’t put yourself in a situation where you’ve missed signal to the market and then you have an even bigger problem on your hand.

Second of all, you know, you should have a dedicated security executive.
NowSecure is a 120 person startup and we have a dedicated security executive. So if you’re bigger than us, you can do it.
Otherwise security is just going to be, you know, the other, another thing on that executive’s list and it’s not going to be getting the attention that it clearly needs. (and perhaps something they don’t feel like an expert in)

I think a best practice that we’re starting to see is risk committees and there’s different names for these.
You know, again, it’s predominantly reporting into audit committees, but audit committees are very busy and a lot of times the expertise on audit committee is financial and audit and compliance.
As we think about the unique challenges that cybersecurity is posing for companies, you know, having a committee that specifically has the time and some of the expertise to focus on that makes a lot of sense.
So risk committee, cybersecurity committee, whatever it happens to be, I think we’ll tend to see over time this, this ends up being a best practice.

A board cybersecurity expert.
Now this was actually something that the SEC originally included in their, in their requirements and they took public comment and they actually ended up removing it.
And so, you know, the general thinking here is that cybersecurity risk is enterprise risk, which is a great thing.
But at the same time, so while you don’t necessarily have to go hire a cybersecurity expert to your board, you really need to have folks on your board that are asking the right questions, that understand the space.
And so I think a cybersecurity expert would make a lot of sense.
But they could be something that’s more, you know, somebody that’s on a technology, an IT, a digital transformation site.
Just at a minimum really can appreciate some of the complexities behind technology and ask some of those really important questions that as fiduciary board members you’re asking to make sure the right controls and governance are in place.

Specific reporting frequency.
I wouldn’t go out there and say like we report to the board as needed or regularly.
Like just be specific about it.
I think you should do it quarterly, right?
I mean you could do it biannually.
I don’t think annual is a good idea.
But if you out, if you’re out there and you put dedicated time, sure there’s a set of KPIs you can walk through.
But stay out of the security weeds.
Take it back to overall risk.
Look at the trends that are going on in the industry.
Talk about how you’re, you know, managing some of the risk through like let’s say insurance.
A bunch of different things to talk about at a board level.
But it ought to be done on a consistent, frequent basis.

Also talked about this earlier, use a framework.
Again NIST cybersecurity framework V2 is now out.
It’s the most reference framework.
I think it’s only going to get better.
So I would take a really, really hard look and ask yourself is, you know, if you’re not going to use that one, ask yourself why.
And you know, there are good reasons to use ISO, COSO, COBIT, NIST 800-53, or CMMC etc.
But you know, this is one to take a real hard look at.

Enterprise risk management.
Again, we’re seeing this in the larger companies.
I think in general an ERM program makes a lot of sense.
And I think even if you’re a smaller company, you can implement ERM.
It doesn’t have to be a big, huge, massive process.
But looking at risk across the board, including cybersecurity risk and helping kind of raise that to the right level of visibility and putting the right investments and strategy in place to deal with that risk is definitely a best practice.

And then, in a nod to what I do all day long, don’t forget mobile risk.
70 to 75%, I think, of all Internet traffic is coming through mobile apps.
When I look at companies, I see like the majority of their revenue or their interaction with the customers is coming through mobile.
And you know, honestly, I see very, very little mobile mentioned in terms of overall cybersecurity risk in 10-Ks.
And so, you know, so much of that revenue is going through mobile.
And a lot of times it’s just kind of being thrown in with security programs that manage web risk but that’s not a great idea. They are very different technologies, architecture, thread models, and risks.
When I was out in Denver, I had a series of six or seven questions that were really great.
I did capture the audio from those.
So I’m going to go ahead and post them on the blog.
And you can hear the audio and see the question and answer session or question response session.

But other than that, if you are interested in chatting, you can go out and connect with me on LinkedIn.
You can hit my personal website and see all of my different social and connect with me on Mastodon or whatever.
This is a really fun and interesting topic.
And I think there’s a lot more coming down the road.
So thanks so much for watching.
Thank you.
Page last updated on March 17, 2024